Nmap is the de facto industry standard network scanner. It can be installed on a variety of operating systems such as Windows, Mac, and Linux, and it can be used via a command line interface or with a graphical interface (the interface itself is known as Zenmap).
Why is Nmap so popular? Because it’s fast, free, open source, and very capable as it can perform not just ping sweeps, but port scanning, service identification, and operating system detection as well. Furthermore the various types of scans it performs are highly configurable.
From the command line/shell prompt, Nmap is invoked with the command nmap. The default nmap command scans hosts with the standard TCP connect method and known ports.
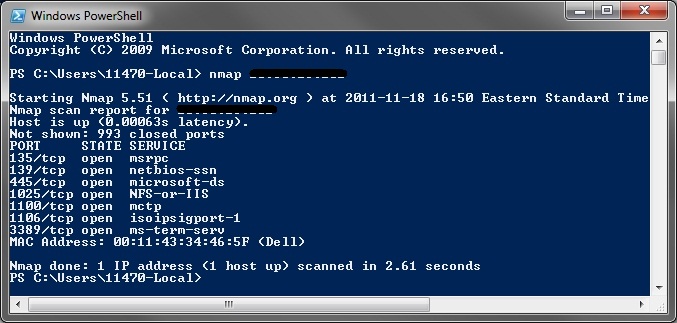
Default Nmap scan on a Windows Server 2003 host.
Jump to:
The nmap command can be customized with parameters called switches, and switches can be passed various values. For example, in the command nmap -sS 192.168.1.10 -p 22, 80 the switches are -sS and -p and the values are 192.168.1.10 and ports 22 and 80, respectively. The following is a summary of some of the more popular switches.
Nmap switch | Scan (-s) Type |
|---|---|
| -sA | ACK scan |
| -sF | FIN scan |
| -sI | Idle scan |
| -sL | DNS (List) scan |
| -sM | Maimon scan (same as NULL, FIN, and Xmas except that the probe is FIN/ACK) |
| -sn | No port scan after host discovery (only print hosts that responded to the scan) |
| -sN | NULL scan |
| -sO | IP protocol scan |
| -sP | Ping scan (also sends ACK and SYN; reference) |
| -sS | SYN scan |
| -sT | TCP Connect scan |
| -sU | UDP scan |
| -sV | Enables version detection |
| -sW | Windows scan |
| -sX | XMAS tree scan |
| -sY | SCTP scan |
| -sZ | Cookie-Echo scan (also see here) |
Nmap switch | Ping (-P) Type |
| -PA [port_list] | TCP ACK Ping |
| -PE | Ping with ICMP type 8 (echo request) and type 0 (echo reply) |
| -PI | ICMP ping |
| -PM | Ping with address mask query |
| -Pn | no ping; previously -P0 and -PN. |
| -PO [protocol_list] | IP protocol ping |
| -PP | Ping with timestamp query |
| -PR | Arp ping. |
| -PS [port_list] | SYN ping |
| -PT | TCP ping |
| -PU [port_list] | UDP ping |
| -PY [port_list] | SCTP ping |
Nmap switch | Output (-o) type |
| -oA | All output |
| -oG | Greppable output |
| -oN | Normal output |
| -oS | Script kiddie output |
| -oX | XML output |
Nmap switch | Timing (-T) type |
| -T paranoid or -T0 | Slowest scan; 300 seconds between scans |
| -T sneaky or -T1 | Slow; 15 seconds between scans |
| -T polite or -T2 | Normal; serial scan; 4 seconds between scans |
| -T normal or -T3 | Normal; parallel scan |
| -T aggressive or -T4 | Parallel scan; 300 second timeout, 1.25 seconds per probe |
| -T insane or -T5 | Parallel, 75 second timeout, .3 seconds per probe |
Nmap scan types
To determine what type of scan to launch with Nmap, you need to understand 1) the differences among the scans available and 2) the types of flags TCP adds to the packets it processes. Scan type | Description |
|---|---|
| ACK | Uses the ICMP ‘destination unreachable’ message to determine which ports are open on firewalls. |
| FIN | Packets are sent with the FIN flag set. Open ports do not respond; closed ports respond with RST/ACK packets. Windows hosts will not respond. |
| IDLE | Uses a spoofed source IP address to send SYN packets. Ports are determined by IP header sequence numbers. |
| NULL | Like it sounds, NULL scans send packets with no TCP flags set. Designed for Unix/Linux hosts (Windows hosts will not respond). |
| SYN | A half-open scan because it will not complete the TCP three-way handshake. |
| TCP Connect | Uses the standard TCP three-way handshake to establish sessions with network hosts. The most reliable type of scan. |
| XMAS | So called because packets are sent with “all the lights on”, i.e., packets are sent with the FIN, URG, and PSH flags set. Open ports will not respond; closed ports will respond with a RST/ACK packet. Windows hosts will not respond. |
TCP flags
TCP Flags | Description |
|---|---|
| ACK | An acknowledgement to SYN flags. Establishes the connection between hosts. |
| FIN | Closes the communication session. |
| PSH | Forwards (pushes) any buffered data. |
| RST | Resets the connection (forces a termination of communications in both directions). |
| SYN | Initiates a connection between hosts and the negotiation of parameters and sequence numbers. |
| URG | Indicates that data in packets must be processed urgently. |
Nmap sample commands
Here are some examples of some common and useful Nmap commands that you can try out. Nmap command examples | Description |
|---|---|
| nmap 203.23.192.1 | Perform the default Nmap scan on host 203.23.192.1. |
| nmap 203.23.192.0/24 or nmap 203.23.192.* | Scan all hosts in the 203.23.192.0 network. |
| nmap -sP 203.23.192.1 | Just pings the host and reports if the host is up or down. |
| nmap -sS 203.23.192.1 | In a stealth scan a SYN packet is sent to the host and Nmap waits until a SYN from the target host is received to see whether the port is open or closed. Nmap does not make a full connection which reduces the chance of being discovered by an IDS or of being found in log files. |
| nmap -sS 203.23.192.1 -O -p 22,80 | Scans the target host for ports 22 and 80 and displays the operating system and its version. |
| nmap -sV 203.23.192.1 -p 53 | Detects the version of the service running on port 53 of the scan target. |
| nmap -v -n -sS -sU -sR -sV -P0 -p- -A -oA scan 203.23.192.1 | -v invokes verbosity. -n skips name resolution. -sS is a SYN scan. -sU scans UDP ports. -sR checks RDP services. -sV tries to verify what is listening on found ports. -P0 skips pinging. -p- scans all 65000 ports. -A enables both OS fingerprinting and version detection. -oA scan creates reports as scan.nmap, scan.gnmap, and scan.xml. |
| nmap -sS -sU -T4 -A -v -PE -PP -PS21,22,23,25,80,113,31339 -PA80,113,443,10042 -PO –script all | Slow comprehensive scan (similar to the Zenmap one below). |
| nmap -T4 –max_rtt_timeout 200 –initial_rtt_timeout 150 –min_hostgroup 512 –max_retries 0 -n -P0 -p80 | Fast scan on port 80. |
| nmap -sP -PE -PP -PS21,23,25,80,113,31339 -PA80,113,443,10042 –source-port 53 -T4 | Ping scan on various ports using a source port of 53. |
| nmap -sP -PE -PS22,25,80 -PA21,23,80,3389 -PU -PO –traceroute | Traceroute scan on various ports. |
Zenmap
This is a screenshot of Zenmap, the Nmap front-end graphical interface. It is useful because it contains several types of scans built in by default.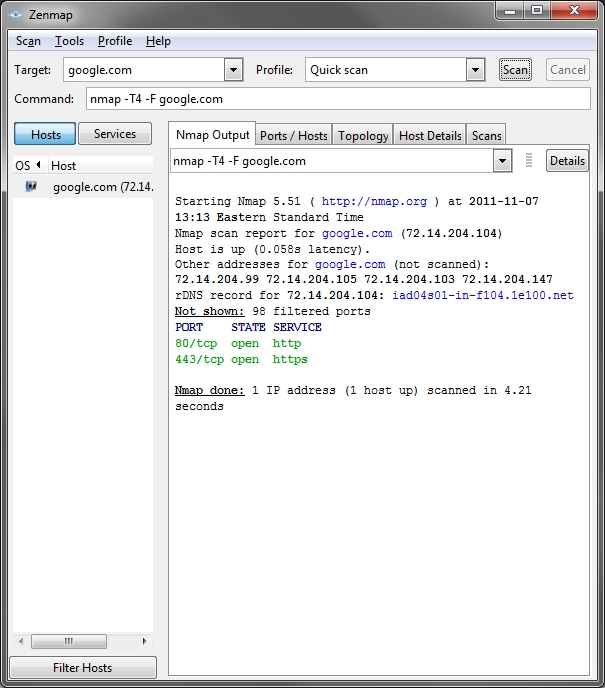
Zenmap, the Nmap graphical interface
Zenmap command name | Nmap command syntax |
|---|---|
| Intense scan | nmap -T4 -A |
| Intense scan plus UDP | nmap -sS -sU -T4 -A |
| Intense scan, all TCP ports | nmap -p 1-65535 -T4 -A -v |
| Intense scan, no ping | nmap -T4 -A -v -Pn |
| Ping scan | nmap -sn |
| Quick scan | nmap -T4 -F |
| Quick scan plus | nmap -sV -T4 -O -F –version-light |
| Quick traceroute | nmap -sn –traceroute |
| Regular scan | nmap |
| Slow comprehensive scans | nmap -sS -sU -T4 -A -v -PE -PP -PS80,443 -PA3389 -PU40125 -PY -g 53 –script all |
Further reference
More information on Nmap can be found in the official Nmap Reference Guide, the official Nmap Tutorial, and the Wikipedia entry for Nmap.Bonus: what if Microsoft had written Nmap?
All Nmap options (except those previously noted)
Sourced from the online Nmap reference guide; go there for even more details. Nmap switch | Description |
|---|---|
| -A | Enables OS detection (-O), version detection (-sV), script scanning (-sC), and traceroute (–traceroute). |
| –adler32 | Asks Nmap to use the deprecated Adler32 algorithm for calculating the SCTP checksum. If –adler32 is not given, CRC-32C (Castagnoli) is used. |
| –allports | Prevents Nmap from excluding any ports during service and version detection. |
| –append-output | Appends to (rather than clobbers) the specified output files. |
| -b [FTP relay host] | FTP bounce scan. These proxy FTP connections allow a user to connect to one FTP server and then request that files be sent to a another server. This scan can be used to ask the FTP server to send a file to each interesting port of a target host, which causes the FTP server to port scan the target. |
| –badsum | Sends packets with bogus TCP/UDP/SCTP checksums. |
| -d or -d [level] | Increases the output debugging level, or specifies the output debugging level to the value specified in [level] (for example, -d9 sets the level to nine). Use -dd for greater effect. |
| -D [decoy] [decoy2] [you] | Launches a decoy scan which makes it appear to the remote host that the host(s) you specify as decoys are also scanning the target network. Consequently an IDS might report multiple port scans from multiple unique IP addresses, but it won’t be able to determine which IP address was scanning them and which IP addresses were innocent decoys. This technique can be defeated through router path tracing, response-dropping, and other active mechanisms. [you] represents your real IP address. |
| –datadir [directory] | Specifies a custom location for the Nmap data files (nmap-service-probes, nmap-services, nmap-protocols, nmap-rpc, nmap-mac-prefixes, and nmap-os-db). |
| –data-length [num] | Appends the specified number of random bytes to sent packets. |
| –defeat-rst-ratelimit | Slows Nmap down to deal with host rate-limiting of RST (reset) packet responses. |
| –dns-servers [server1] [server2] | Specifies alternate DNS servers to use (instead of the ones listed in resolv.conf or the Windows registry). |
| -e [interface] | Uses the specified interface for Nmap to send and receive on. |
| –exclude [host1],[host2] | Specifies a comma-separated list of targets to be excluded from scans. The targets can be specified by IP addresses, host names, octet ranges, etc. |
| –excludefile [file] | Specifies a file containing targets to be avoided by scans. |
| -f or -f –mtu [value] | Fragment packets (or optionally fragments them with the given MTU value). The intention is to split up the TCP header over several packets to make it harder for firewalls and IDSs to detect scan activity. |
| -F | Enables fast mode for scans (fewer ports scanned; 100 instead of 1,000). |
| –fuzzy | Configures Nmap to guess which operating system a target is running. Same as –osscan-guess. |
| -g | Specifies the source port number for packets sent. Same as –source-port. |
| -h or –help | Prints the Nmap Help summary page. |
| –host-timeout [time] | Tells Nmap to give up on target hosts after the specified amount of time passes. For example, 30m specifies thirty minutes. |
| –iflist | Prints host interfaces and routes in output (for debugging). |
| -iL [file] | Configures Nmap to read the list of targets specified in [file]. |
| –initial-rtt-timeout [time] | Sets the initial running timeout value for determining how long Nmap will wait for a probe response before giving up or retransmitting the probe. |
| -iR [number_hosts] | Tells Nmap how many random target IPs to generate. |
| –ip-options [options] | Sends packets with the specified IP options. These options are described here. |
| –log-errors | Logs output errors and warnings to the normal-format output file. |
| –max-hostgroup [num_hosts] | Specifies the maximum size of host groups for parallel port scans and version scans. |
| –max-os-tries [number] | Sets the maximum number of OS detection tries against a target. By default Nmap will makes five attempts. |
| –max-parallelism [num_probes] | Specifies the maximum number of probes that may be outstanding for a host group. This can be set to a value of one to prevent Nmap from sending more than one probe at a time to hosts (same as the –scan-delay option). |
| –max-rate [number] | Sends packets no faster than the specified number per second. For example, a value of 100 will limit transmission to one hundred packets per second; a value of 0.1 equals one packet every ten seconds. |
| –max-retries [number] | Specifies the maximum number of times that Nmap should retransmit port scan probes. The default is ten retransmissions. |
| –max-rtt-timeout [time] | Sets the maximum running timeout value for determining how long Nmap will wait for a probe response before giving up or retransmitting the probe. |
| –min-hostgroup [num_hosts] | Specifies the minmum size of host groups for parallel port scans and version scans. |
| –min-parallelism [num_probes] | Specifies the minimum number of probes that may be outstanding for a host group. A common usage is to set –min-parallelism to a number higher than one to speed up scans on laggy hosts or networks. |
| –min-rate [number] | Configures Nmap to send packets at least as fast as the value specified. For example, a [number] value of 300 means that Nmap will try to transmit at a speed of 300 packets per second or more. |
| –min-rtt-timeout [time] | Sets the minimum running timeout value for determining how long Nmap will wait for a probe response before giving up or retransmitting the probe. |
| -n | Configures Nmap to skip reverse DNS resolutions on the IP addresses it encounters, which scan speed up scans. |
| –no-stylesheet | Prevents the association of XSL stylesheets with XML output. |
| -O | Enables operating system detection. |
| –open | Shows only open (or possibly open) ports in output. For when you don’t want to see the ports that are closed, filtered, and closed|filtered. |
| –osscan-guess | Configures Nmap to guess which operating system a target is running. Same as –fuzzy. |
| –osscan-limit | Limits OS detection to hosts that Nmap considers promising (hosts that have at least one open port and one closed port). |
| -p [port_range] | Configures Nmap to scan only the specified ports. Examples are: -p22; -p1-65535; and -p U:53,111,137,T:21-25,80,139,8080,S:9 |
| –packet-trace | Shows all packets sent and received during the scan in the output. |
| –port-ratio [ratio] | Scans ports in nmap-services with a ration greateer than the value specified by [ratio] (must be between 0.0 and 1.1). |
| –privileged | Configures Nmap to assume that the scanning user is fully privileged on the target hosts. |
| -r | Configures Nmap to scan ports in consecutive (low to high) order. By default it scans ports in a random order. |
| -R | Configures Nmap to always attempt to resolve IP addresses to host names. |
| –reason | Configures Nmap to display the reason why a port is reported to be in a particular state. Can also be set by -d. |
| –release-memory | Causes Nmap to release allocated memory just before it quits. Useful for memory-leak debugging. |
| –resume [file] | Configures Nmap to record new scan results in the output file from a previous, aborted scan. |
| -S [IP_address] | Sets a spoofed IP source address. |
| –scan-delay [time] | Configures Nmap to wait at least the given amount of time (such as 1s between each probe it sends to a target. Useful for rate limiting and dealing with IDS. |
| –scan-flags [flags] | Create your own customized scans by specifying the TCP flags (see below) you want to use. For example, –scanflags URGACKPSHRSTSYNFIN (sets everything). |
| -sC | Performs a script scan using the default set of scripts. Same as –script=default. |
| –script [file | category | directory] | Runs a script scan using the specified comma-separated list of file names, script categories, and directories. The Nmap Scripting Engine is described here. |
| –send-eth | Configures Nmap to send packets at the raw Ethernet layer instead of the IP (network) layer. By default, Nmap chooses the one which is generally best for the platform it is running on (raw sockets (IP layer) for Unix; Ethernet frames for Windows). The opposite of –send-ip. |
| –send-ip | Configures Nmap to send packets over raw IP sockets rather than lower level Ethernet frames. The opposite of –send-eth. |
| –servicedb [services_file] | Configures Nmap to use the specified services file rather than the default nmap-services data file. |
| –source-port [portnum] | Specifies the source port number for packets sent. Same as –source-port. |
| –spoof-mac [mac_address/prefix/vendor_name] | Configures Nmap to use the specified MAC address for all raw Ethernet frames it sends. If the address provided is 0 (zero), Nmap will supply a randomly generated MAC address for the session. |
| –stylesheet [path/URL] | Specifies the XSL stylesheet to transform XML output to formatted HTML. |
| –system-dns | Configures Nmap to use the OS’s (system) name resolver instead of the name servers configured on your host. The system resolver is always used for IPv6 scans. |
| –traceroute | Configures Nmap to launch a traceroute scan against the target. |
| –top-ports [number] | Configures Nmap to scan the specified number of highest-ratio ports found in the nmap-services file. |
| –ttl [value] | Sets the IP time-to-live field to the given value. |
| -v or -v [level] | Increases the output verbosity level (causes Nmap to display more details about the scan in progress). Use -vv to further increase verbosity or set the level directly with -v2, -v3, … |
| -V | Displays the version number of Nmap (for example, version 5.51). |
| –version-all | Configures Nmap to try every service and version probe against each port. |
| –version-intensity [level] | Specifies an intensity level (0 – 9) for -sV. The higher the number, the more likely the service will be identified accurately and the long ther scan will take. The default intensity level is 7. |
| –version-light | An alias for –version-intensity 2. |
| –version-trace | Configures Nmap to display detailed debugging information about what its version scan is doing. |
| –webxml | An alias for –stylesheet http://nmap.org/svn/docs/nmap.xsl. |

No comments:
Post a Comment